Cryptography and Network Security Simplified

For secure data transmission via Internet or any public network, there is no alternative to cryptography. Many of us either knowingly or unknowingly using cryptic messages while purchasing or transferring money online.Governmental and intelligence agencies around the world use cryptography to transmit message securely through public network. Without cryptography all message in Internet are unsecure. You might be thinking what about the security of email we send daily- no email is secure until email system using data encryption technology. So, whenever you send some confidential business information to your clients, make sure you always use cryptography. In this hub I will discuss little bit of history and basics of cryptography-mainly modern day cryptography. Once you read this hub carefully, you will be confident enough to determine which cryptography to use when, because every crypto algorithm has it strength and weakness
Contents
1. History of cryptography
2. Cryptography Concept
3. Basic goals of cryptography
4. Cryptography Keys
5. Symmetric key algorithm
6. Asymmetric key algorithm
7. Hashing Algorithms
History of cryptography
History suggests that Roman Emperor Julius Caesar was the first in the history, used cryptography to safeguard his messages sent to his generals while he was trying to conquer Europe. Caesar started using cryptography when his messengers were frequently being ambushed while on the way to his deployed military forces. His invented cryptography is now known to modern world as “Caesar Cipher”- in this system of message encryption technique he used to shift letters of his original message only 3 digits to the right. For example in a message if a word start with ‘a’, then he used to write it ‘d’ to keep his original message unintelligible to his enemies. This was very basic and simple cryptography is also known as the ROT3 or rotate 3 or C3 cipher-more generic term is substitution cipher.
Ultra and Enigma-Just before the World War II, German military designed a coding machine to encrypt all the governmental messages-this machine was nicknamed as Enigma. And truly its encoded messages remained enigmatic to the enemies. This machine used a series of rotors to encode a message into a substitution cipher. The only way to decode this message was to use another machine with similar rotor settings. This enigma code was matter of huge frustration to the allied forces during the World War II, because they have no machine like enigma. In an effort to uncover enigma messages, allied forces started a code breaking operation known as “Ultra”. Eventually they become successful when the Police military constructed a prototype of the Enigma. In 1940, the first enigma code was broken by the allied force. At that time Japan also used similar type of cryptography machine called “Japanese Purple Machine”
Cryptography Concept
In crypto world, you will hear the terms like “codes” and “ciphers”. Though many used both codes and ciphers interchangeably, but they are not the same.
When you write a message with you own language, it is just a plaintext. If you want to make you plaintext message to make unintelligible to anyone other than you, then you use a cryptographic algorithm to encrypt the message. Actually, cryptographic algorithms encrypt a plaintext message into a cipher text message. Now, if you send that message to a person he can only read the message if he uses the same algorithm to decrypt it.
Plaintext (your email)>cryptographic system> cipher text…media….cipher text>decryption algorithm>plaintext message.
Goals of Cryptography
Every cryptography has four basic goals-confidentiality, integrity, authentication and nonrepudiation. Every algorithm ensures that these four goals are met while transmitting any digital message.
Confidentiality- this ensures that while transmitting date in a network or Internet, it will remain confidential. No one can read this message except your intended receiver. The two types of key systems in use for confidentiality- public key and secret key.
Integrity-this ensure that a message is not altered in the way of transmission. So, a receiver of the message becomes certain that his received message is identical to the original message- no alteration of message by a third party. This functionality is ensured by digitally signed the original message.
Authentication- this is a very important function of crypto system and it verifies the claimed identity of the users. For instance, Dan wants to communicate with one of your friend, Jim. Jim sends Dan a challenge message by saying that proves your claim by encrypting the message. Then, Dan encrypts the message with his secret key only known to him and Jim. The encrypted message is sent back to Jim and after his verification that the encrypted message matches with the original message, he become sure that he is communicating with Dan.
Nonrepudiation-this gives assurances to the receiver of a message that it actually came from the sender and no one is faking the identity of the sender. This function of cryptography is provided with Public Key System only.
Cryptographic Key
In early day of cryptography, experts used to believe that secrecy of the algorithm will keep it safe from compromising the secrecy of encrypted messages. Unlike that, modern encryption algorithm is open to all for review and the secrecy is maintained by the use of keys. As long as you keep your key secrets, your messages are safe. The strength of the encryption depends of the length the keys-the longer the keys the better the security. As long as the computing power will keep increasing the length of keys also keep going up. Higher computing power will eventually make today’s standard key length obsolete. Once, the 56 bit key of DES algorithm was considered secure, but today 56 bit DES is no more in use. To keep data safe from prying eyes, most of the modern algorithm use 128-bit key.
There are number of cryptographic algorithms used for encryption data and most of all fall into two generic categories- Public Key system and secret key system.
Symmetric Key Algorithm
It is also known as secrecy key or shared key algorithm. Because in symmetric key algorithm a shared key does both the encryption and decryption. Since only one is used for doing everything, so the success of this algorithm depends on two factors-secrecy of the key and its distribution
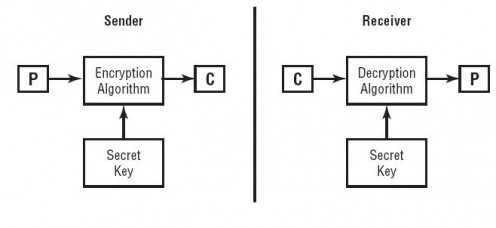
Strength and weakness of Symmetric Key Algorithm
Strength
| Weakness
|
Faster than asymmetric key algorithm- often 1000 times faster at least
| Distribution of the key is the problem. because once a compromised key means a total security leak
|
Hardware implementation of this algorithm is possible
| It does not provide nonrepudiation of data
|
Once a member of a security group leaves a new key must be generated and distributed.
|
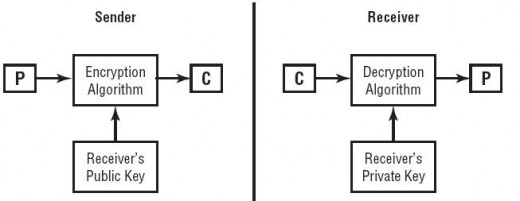
Asymmetric Key Algorithms
It is also known as public key algorithm and it covers up all the weakness found in symmetric key system. In this algorithm, there are two keys-public and private- used for encryption and decryption. Public key is shared to all, and each member of a group had his own private key, which is only known to him. Normally, the public key is used to encrypt the message and private key is used to decrypt the message. The pair combination of public and private key is unique. If a public key is known to outsider also, he cannot decrypt the message because he does not have the other side of the decryption key-the private key-which never being transmitted in the network, always remains inside a computer. So, the thing his if you encrypt a message with the public key and send it to your friend via Internet, then only your friend’s private can open this message, no one else in this world. Thus making a public key encryption system an extremely efficient and confidential crypto system of the world.
Asymmetric key algorithm also provides the functionality of digital signature.
Symmetric and Asymmertic algorithms Comparison
Symmetric
| Asymmetric
|
|---|---|
Single shared key
| Key pair sets
|
Key distribution must be secure
| Public key is available to all, only private key need to be secured.
|
Algorithm not scalable
| Scalable algorithm
|
Bulk encryption
| Used for small amount of data encryption, digital signature, digital certificate (CA)
|
This algorithm provides confidentiality only
| It provides Integrity, authenticity, nonrepudiation
|
Hashing Algorithms
Hashing is mainly used with digital signature, it provides a fixed length digital digest of a message and it is almost impossible to derive a message from its hash function. It is also very much unlikely that the two messages will generate the same hash function-thus a very effective way to ensure integrity of a message. Most commonly used hash algorithms are:
Message Digest 2 (MD2)
Message Digest 4 (MD4)
Message Digest 5 (MD5)
Secure Hash Algorithm (SHA)
Hash-Based Message Authentication Code (HMAC)
Symmetric Cryptography Algorithms:
- Data Encryption Standard (DES)
- Triple DES (3DES),
- International Data Encryption Algorithm (IDEA),
- Blowfish
- Skipjack,
- Advanced Encryption
- Standard (AES).
Asymmetric/ public key algorithm
- Diffie-Hellman
- RSA Public Key Encryption
Cryptographic algorithm development is a never-ending race as the cryptanalysts are also getting smatter with the advent of higher computer power of decoding secret codes. As a user you do not need any advanced level of knowledge how cryptographic algorithm works in a networked environment. You just need to know the difference between symmetric and asymmetric algorithms so as you can make right choice when to use which one of them to make your digital data transmission both cost effective and secure. Can you guess if you have to send one terabyte of data over a 512Kbps line then which algorithm will be most efficient- you’re right, symmetric key algorithm, because it’s much faster?








